Daphne && Athos - E01:
In this first episode, we will learn some Infosec basics through the adventures of Daphne and her evil brother Athos.

Contents
Summary
Synopsis / TL;DR [Spoiler Alert :D]
- Daphne buys a computer and she sets a password to use it
- Athos manually guesses the password
What you will learn:
- Infosec basics
- CWE / CVE
- Password guessing
- GNU Linux terminal basics
- Password setup on GNU/Linux
- SUDO
- The MOTD
What you will need
- A computer
- A GNU/Linux operating system
Scenario
Daphne, a young Infosec enthusiast buys a Raspberry Pi computer to start learning about programming. Once she unboxes it, she is greeted by a black screen asking for a login.
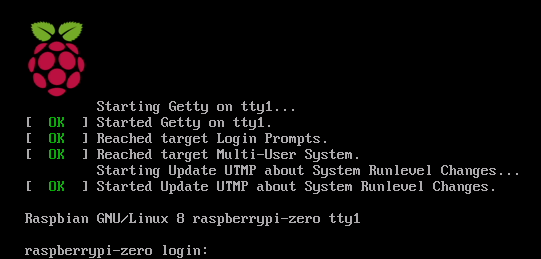
She has no idea of what's the username nor the password to use, but a quick look at the computer manual shows that the username is pi and the password is raspberry.
Daphne proceeds then to write pi as instructed and then she presses Enter
Now the system asks for a password; she writes raspberry and once again she proceeds to press the Enter key.
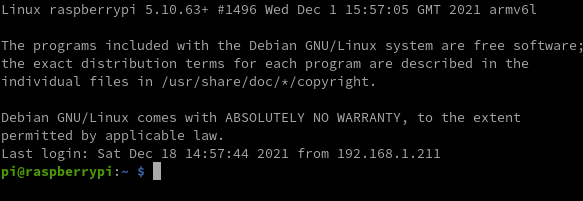
Now the manual tells her that if she's seeing this, she was able to successfully login into her new computer. Now Daphne is advised by the manual to setup a new password.
To achieve this, apparently she needs to use the "passwd" command so she writes the following into the terminal:
passwd
and she presses Enter
The system now asks her for a new password. She has to write it twice, so that the system knows that there are no typos in her password.
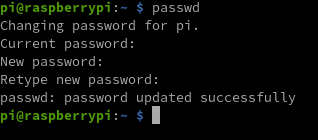
She used a simple password so it will be easier to remember, something like password1 should be fine.
"That's enough for today" she sighs while glancing at her wristwatch; she has other stuff to do so she'll be back on her computer another time.
She checks how to logout in the manual and leaves the computer on. Her brother, Athos, is home and she doesn't want to him to have access to her new computer!
The manual explains that the exit command is just what she needs.
Daphne writes it on the terminal and she presses Enter for the last time (at least today).
Her terminal is back as it was at the beginning, before her first login. She goes on with her afternoon homeworks.
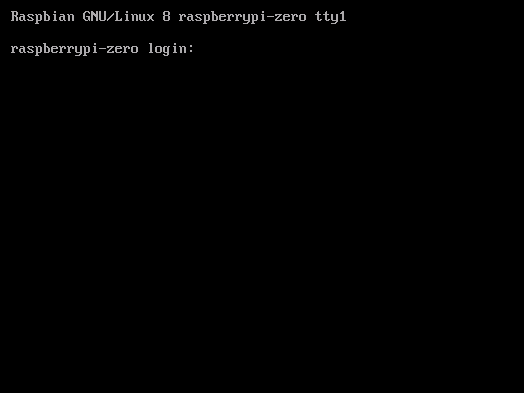
Daphne doesn't know it, but Athos has been spying on her since she went home with this mysterious box. He knows it's a computer and he wants to access it.
He looks at the screen. "Damn it", he says quietly. He recognises a GNU/Linux login screen and he knows a username / password combination is needed.
He quickly grabs the manual on the table near the keyboard and starts browsing it.
Apparently it's a Raspberry Pi.
Athos expression becomes an evil mix of satisfaction and disgust: "It was all too easy".
He already knows what to do: use a classic one, present in almost all Raspberry Pi, pi while the same goes for the password; he unboxed so many of these little computers and he remembers it by heart: raspberry
Pressing keys on the keyboard without even looking at them he already thinks what to do once he has full control over the...
"Damn it! Login failed! Did she change the pi password ?" he mumbles to himself.
Looking at the manual, he sees that indeed the first step after the login is to change the root password. So now the question is: Which password Daphne set up for this system?
Athos doesn't have a lot of time. He quickly thinks about the easiest way under those conditions to access the system; he starts with the obvious: password guessing.
He remembers some of the worst passwords by heart, since he's used the rockyou wordlist so many times... Passwords like that are almost always worth trying:
123456
12345
123456789
password
iloveyou
princess
1234567
12345678
abc123
babygirl
monkey
lovely
654321
qwerty
111111
iloveu
000000
sunshine
chocolate
password1
soccer
....
Failed login after failed login, he begins to lose hope.
"Damn, it's usually almost always one of those!"
He starts thinking about the keyboard layout: "Is there any chance that I'm not writing what I think I'm writing?" It's difficult to tell, since the password is not shown on the terminal when typed.
To counter this, he starts writing the password in place of the username, as it's the only way to display on the screen what he's typing. Then, he deletes it, and puts pi again as the username, before typing under "password" the exact sequence of characters he just wrote.
login: qwerty
"Nice", he says as he looks at the keyboard: a standard QWERTY, which confirms that indeed no weird keyboard layout is installed.
At least not that pesky QWERTZ keyboard layout, otherwise his login would have been qwertz, even if the last key pressed was
He repeats the same method with his mental list of weak passwords, until finally...
Login
password1
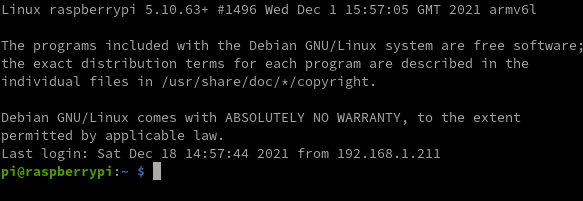
"Bingo!" he thinks. He wants to impress his little sister and looks for a way to make her know that he was able to gain access to her computer.
"Uhmm... I know! The MOTD!"
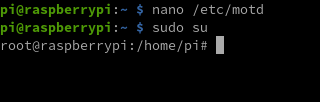
He tries to set it up with his favourite text editor on the terminal: nano
A simple nano /etc/motd should be enough.
While he thinks about what to write, he notices something strange
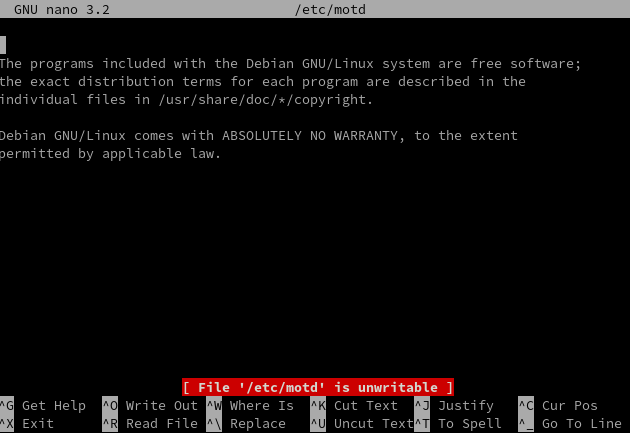
Apparently the motd file is unwritable?
He feels stupid, "of course it is.. I'm not root yet!"
He quickly types sudo su since he knows that almost all Raspberry Pi Operating Systems have sudo installed and the pi user is allowed to perform super-user (or su) operations like, login as root.
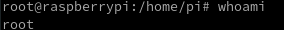
Just to be sure he also uses whois to check that indeed he's root now.
He quickly writes a little message into the file /etc/motd... Something like:
Hi Daphne, you should use a stronger password! :D
Your big brother (watching you)
- Athos
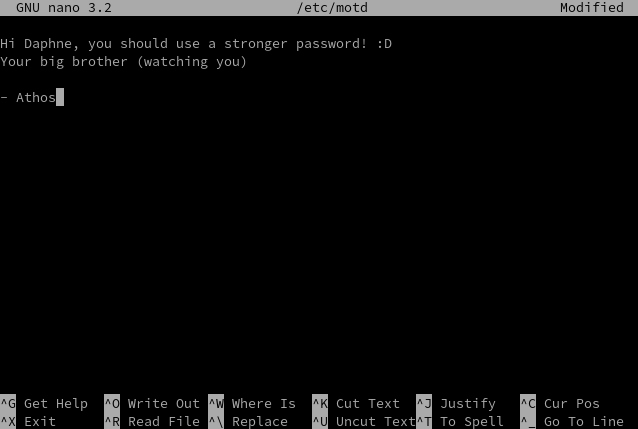
"Yeah, this will do nicely", he thinks.
"With the MOTD setup, she will receive my message on the terminal next time she logs in", he chuckles.
Satisfied, he exits the terminal and leaves the computer on, with the login screen on display.
What have I just read?
First of all, welcome!
If you're confused about everything you just read, this section is for you!
In this first episode of "Daphne && Athos", our lovely couple of siblings, we explore some basics of Infosec.
Infosec , short for "Information Security" is the "art" of protecting data.
In this case, the data is everything stored on Daphne little computer that needs to be defended from Athos.
A simple measure of protection of course is a password: that's what Daphne types on her computer to "login".
A Raspberry Pi is a convenient little computer that allows people around the world to learn coding, develop small projects or have a cheap personal computer and that's exactly Daphne's objective.
Being that convenient and widely adopted however, means also relax some security measures and the "default password" is one of them.
To be fair, even industrial systems and Enterprise appliances still have this bad habit and that's why we have CVEs.
Basically, Infosec professionals all around the world collaborate to put vulnerabilities (like a default password) into a common public database, called C.V.E. or Common Vulnerabilities and Exposures.
Every "CVE" is represented by an unique Id composed by the disclosure year and a sequence number.
Even for the default password on the Daphne's Raspberry Pi there's a CVE, specifically the CVE-2021-38759.
But that's not what Athos uses to access Daphne's data; she followed the system recommendations on changing the default password right away.
However, what Daphne did was to setup a very weak password like password1 and Athos exploited this weekness.
A weak password has no CVE since it's not specific to a system but is rather something common that happens pretty often and everywhere.
That's why it has rather a CWE assigned, or simpliy put a weakness which is defined in the CWE-521.
What Athos did while trying to guess the Raspberry password from a widely-used list of "bad passwords" is actually a technique called "Password guessing". This technique has been executed manually in our case by physically typing on a keyboard , but it could also be the result of an automated program and be called "bruteforce" when hundreds or thousands of passwords are tested every second.
Something we saw in the screenshots above and needs some explications is the GNU/Linux terminal.
Basically, this interaction method is what allows system administrators (and common people as well) around the world to perform tasks on their computer or servers.
Contrary to what most of us see on our computers every day, most of the operations are instead performed in the terminal, hidden by windows and buttons.
Some basic operations like password setup on GNU/Linux systems are pretty straightforward as Daphne experienced; some others require some attention as Athos saw when trying to modify the welcome banner or MOTD to prank Daphne.
That moment in the story touched also "sudo" or Super User DO, which is a program that allows an authorised user to perform operations usually requiring "root" privileges.
In fact, to modify the MOTD on a GNU/Linux system usually we need to be root and Athos achieved this by executing su which is a shortcut to login as Super User but prepended by "sudo" after seeing that his text editor was unable to write the MOTD configuration file (probably due to lack of permissions).
And that's basically it for this episode, if you liked it or if you have any question just let me know.
Stay tuned for more!

